Deciding to store all your precious customer data in the cloud is a huge decision, one not to be taken lightly. Fortunately, when you choose a Salesforce platform, the risk is not only significantly mitigated but it is also a shared responsibility.
Salesforce takes care of the infrastructure that stores your data, keeps it safe, protects it from malfunctions in hardware or software components and protects it from attack by hackers and other types of data theft.
Your responsibility is to protect your data from your internal employees, partners and customers while giving them just enough access to perform the functions they need to be able to do.

Multiple levels of control within Salesforce allow you to secure the environment, functions, and data access.
Salesforce Environment Controls
The first level of access you can control is around the environment, deciding who can login, from where, from when and how.
Who Can Login?
Each individual user requires their own login account to be able to access Salesforce, this account has an associated profile, role, and other functional restrictions. A system administrator typically creates this account, makes the appropriate settings and triggers an email to be sent to the user to login the first time. It is recommended that every user has their own account and accounts are not shared between users. Shared user accounts make it impossible to identify the individual who made changes to records or who exported a report of all your customers to automatically route approval processes to the right individual and for collaboration via Chatter.
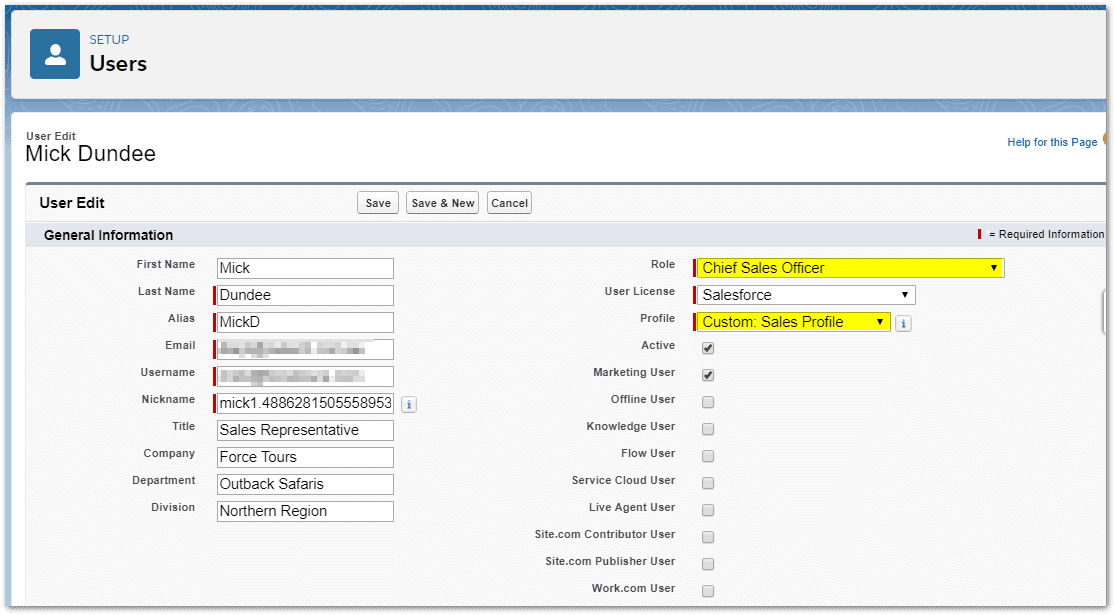
Where can users login from?
Using the Login IP Range settings on user profiles, you can apply an additional level of security permitting users to only login from a specific IP Address range. If your office locations have static IP addresses then it is easy to configure these addresses and allow logins from those locations only. Where it gets difficult is when you have mobile users who connect from a different mobile network every time they access the Salesforce App on their phone or tablet or users that need to be able to connect from their homes after hours. You may want a different profile for these users with less strict limitations.
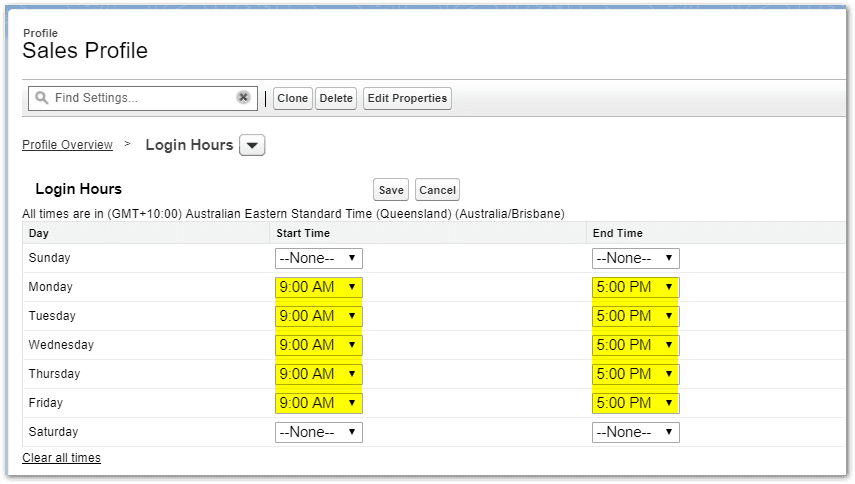
When can user login?
Login Hours can be configured to only permit access during certain times. Mobile users and any users that may need to work outside normal business hours need to be considered when restricting login hours. Login Hours are configured as part of user profiles.
How can users login?
The actual login method can be the standard username and password combination like most websites use or it can be strengthened by two-factor authentication that requires an additional device or app to provide enhanced security.
For standard username/password logins you can also set the complexity of passwords required, how frequently the password must be changed and the minimum length required.
Integrating user accounts with Microsoft Active Directory and other authentication services (eg Google, Facebook, OKTA) allow for single sign-on so users don’t have to remember yet another username and password for Salesforce access.
Explore the Trailhead module User Authentication for further information.
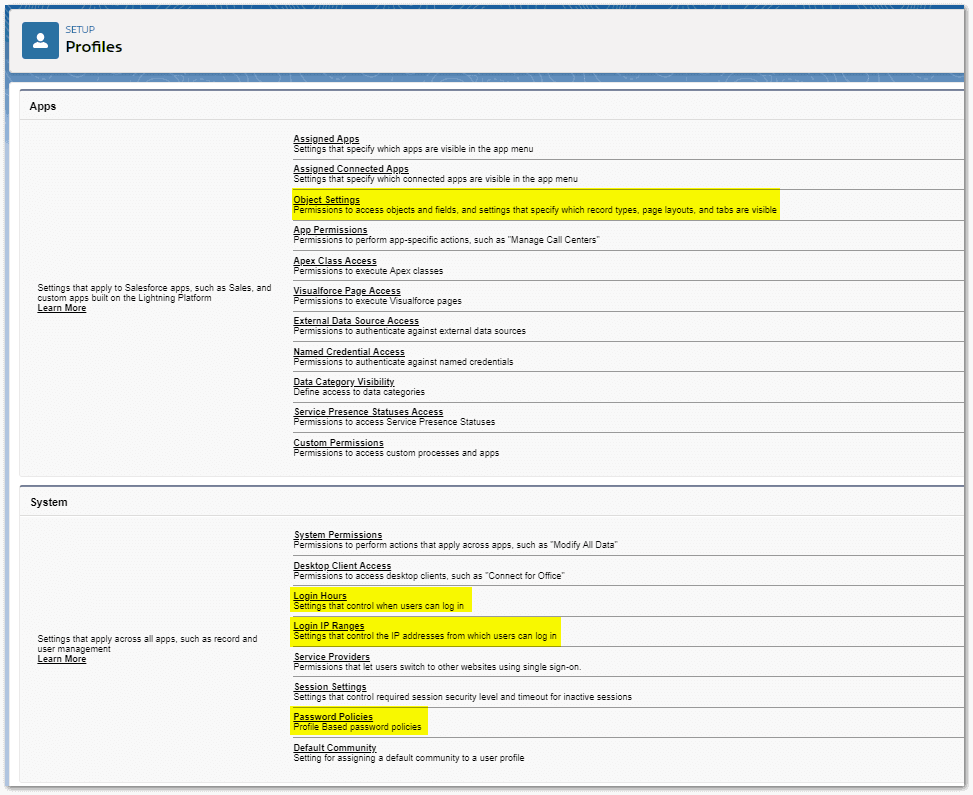
Functional Controls in Salesforce
User Profiles define what each user can do within Salesforce. These include which apps are available from the App Menu, the level of access (read/create/edit or delete) for objects such as contacts, accounts, and opportunities. Field Level Security settings allow access to be controlled down to the individual field level for each profile. Permissions within Apps are also configured within profiles. For example: the permissions to import new leads and to convert leads. Login IP Ranges, Login Hours, and Password Policies are all configured in user profiles. Every Salesforce user is assigned one profile when their user account is created.
Data Access Controls in Salesforce
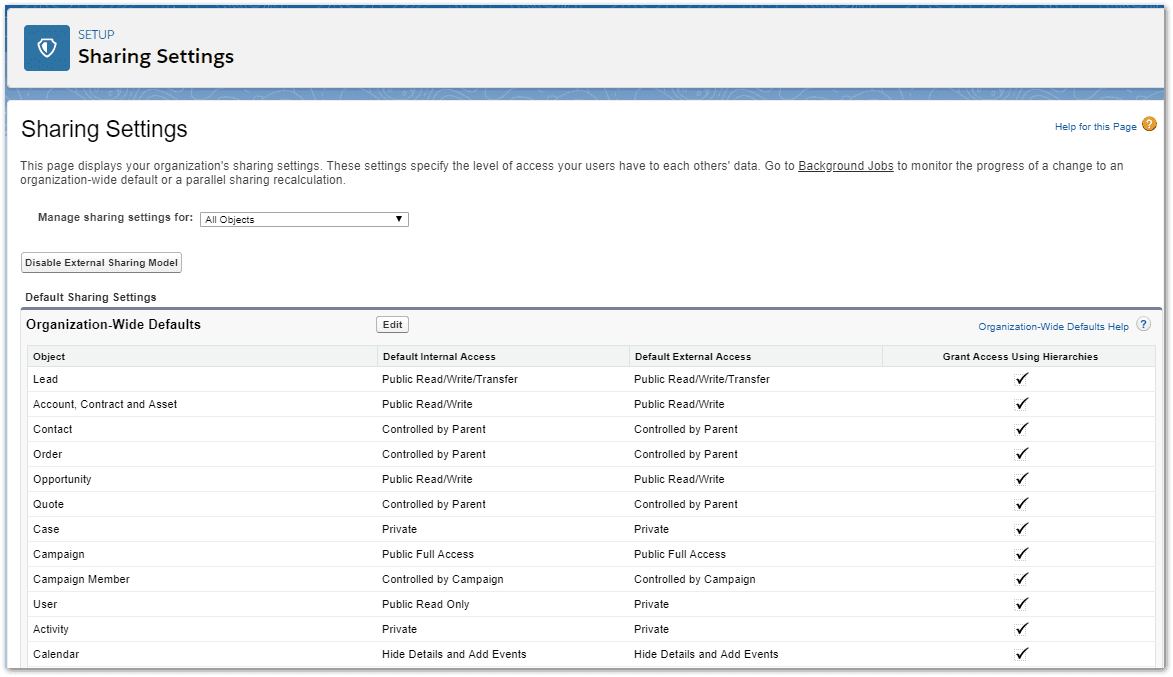
The final component of access that you can configure is access to data contained within Salesforce. A combination of Organizational Wide Defaults, Sharing Rules, Roles, and Data Encryption can provide customized, fine grained control over who can access data records. Configuring these data controls is not for the novice, they need to be carefully planned and configured at the start of your installation and amended as your needs change.
Salesforce offers two types of encryption to protect data: Classic Encryption and Shield Platform Encryption. Classic Encryption is quite limited in what type of fields can be encrypted and Shield is an extra cost product that allows you to encrypt all kinds of data when it is stored in the Salesforce environment.
Summary
Once these security controls are in place, you can configure groups of users to have different views of data and to perform different functions within Salesforce. Customized Record Pages (e.g. for editing an opportunity) can be created and applied to these groups so each group has a different experience. For example – Account managers may see more details on an opportunity record than junior sales reps and the managers may have extra functions that they can perform – like submitting an opportunity for approval to a more senior manager.
The design of an appropriate mix of these security controls can be a complex process that needs to take into account your individual business requirements. Simply accepting all the default values and hoping for the best is not a recommended solution. Salesforce-certified specialists from a partner like KeyNode Solutions can draw on their experience to customize these controls to protect your valuable data. Even perfectly customized security settings may require adjustments as your business grows and gets more employees with different roles. This is where ongoing Salesforce support services could be handy.
Ready to ensure that access to your data in Salesforce is properly setup? Talk to Us!
KeyNode Solutions has helped hundreds of business, including those seeking a Seattle Salesforce Partner, increase their efficiency and revenue. Drop us a line at hello@keynodesolutions.com or call us at (858) 215-5371. We’ll be delighted to help you!
Free Salesforce Implementation Assessment
It takes a few minutes and gives you immediate results.
Use this proven tool to find out how Salesforce platform can increase your revenue.
 KeyNode Solutions is a San Diego Salesforce Consulting Partner company. We deliver the ultimate Salesforce solutions to grow your business: implementation, integration, customization, and development. Our best-in-class Salesforce managed services for ongoing support available nationwide.
KeyNode Solutions is a San Diego Salesforce Consulting Partner company. We deliver the ultimate Salesforce solutions to grow your business: implementation, integration, customization, and development. Our best-in-class Salesforce managed services for ongoing support available nationwide.



